Client Portal Office365 Single Sign-On
Updated
by Jason He
DeskDirector's client portal offers Office 365 Single Sign-On (OAuth) as the recommended login method for users. This authentication mechanism provides a secure and convenient way for users to access the client portal using their Office 365 credentials. By leveraging OAuth, DeskDirector enhances the login experience and offers additional security features, including two-factor authentication (2FA) and the latest security protectors provided by Microsoft.
Benefits of Using OAuth for Client Portal Login:
- Enhanced Security: OAuth provides a more secure authentication method compared to traditional password-based logins. With OAuth, user passwords are not stored or transmitted directly to DeskDirector. Instead, the authentication process is handled by Microsoft's secure infrastructure. This reduces the risk of password-related vulnerabilities, such as weak passwords, password reuse, or interception of credentials.
- Two-Factor Authentication (2FA): DeskDirector leverages the 2FA capabilities provided by Microsoft through OAuth. With 2FA enabled, users are required to provide an additional verification factor, such as a unique code sent to their mobile device or a biometric scan, in addition to their Office 365 credentials. This adds an extra layer of security, making it significantly more challenging for unauthorized individuals to gain access to the client portal, even if the user's password is compromised.
- Compliance with Industry Standards: By utilizing OAuth and integrating with Office 365, DeskDirector aligns with industry best practices and security standards. Microsoft invests heavily in securing their authentication infrastructure, ensuring that OAuth meets stringent security requirements and undergoes regular security audits and updates. By leveraging OAuth, DeskDirector inherits the robust security measures implemented by Microsoft, further enhancing the protection of user accounts and sensitive data.
- Continuous Security Improvements: Microsoft continually enhances the security features and protocols associated with OAuth. They monitor and address emerging threats, implement advanced security controls, and provide regular security updates to address vulnerabilities. By using OAuth for client portal authentication, DeskDirector customers benefit from these continuous security improvements without requiring additional effort or maintenance on their part.
The DeskDirector client portal's Office 365 Single Sign-On (OAuth) offers numerous benefits over traditional password-based logins. It enhances security, provides the option for two-factor authentication (2FA), enables centralized user management, complies with industry standards, and leverages continuous security improvements provided by Microsoft. By default, OAuth is enabled for all newly registered customers, offering a robust and convenient login experience while ensuring the highest level of security for accessing the client portal.
Configuration
You can enable or disable Office365 SSO in Authentication settings, which you can access from System/Authentication/Client Portal Office365.
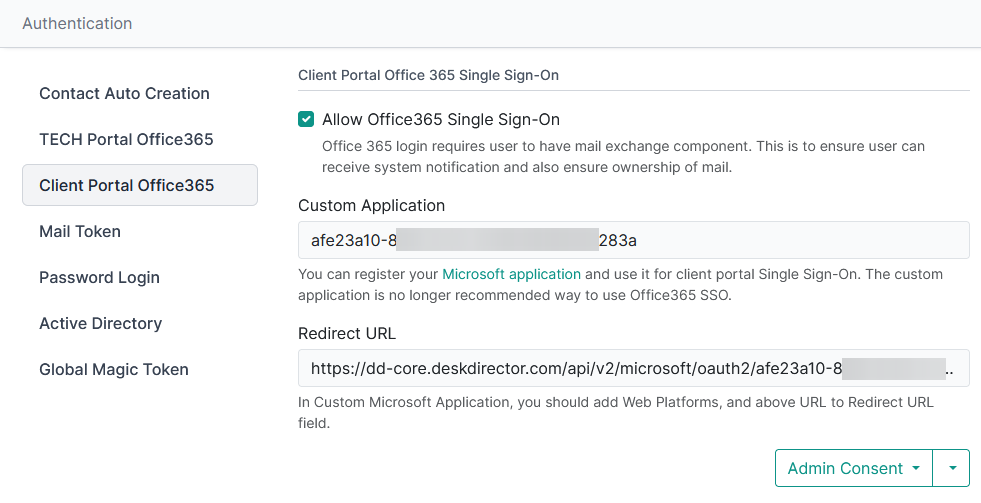
Custom Application
DeskDirector has recently introduced a streamlined approach for enabling Single Sign-On (SSO) in the client portal, eliminating the need for customers to register their own application in the Azure Portal. Previously, customers had the option to register a custom application, but this process required complex configuration and ongoing maintenance to ensure its functionality. Additionally, the custom application's secret had a limited lifetime, necessitating regular updates.
With DeskDirector's latest enhancement, SSO can now be enabled without the requirement of a custom application. Instead, DeskDirector utilizes its own registered application for OAuth. This approach simplifies the setup process for customers as they no longer need to register an application, configure settings, or manage secrets. Moreover, DeskDirector's registered application is approved and certified by Microsoft, ensuring a secure and reliable authentication experience for users.
In the past, the custom application provided customers with the ability to display their own branding during the OAuth consent process, where the application would request permission to access user profiles. However, with the introduction of admin consent, tenant administrators can grant consent on behalf of all tenant users. As a result, the streamlined login flow eliminates the need for the consent page, making the custom application unnecessary. Customers can continue to utilize their custom application until DeskDirector announces its full end of support.
By leveraging DeskDirector's default application for SSO, customers can enjoy a simplified setup process and reduced maintenance efforts, while still benefiting from a secure and seamless authentication experience in the client portal.
Q: Why DeskDirector deprecated custom application?
A: Custom application is never a legit way to perform OAuth. The application should be owned by the software service provider, not by customer. The responsibility of reading user profile should be taken by DeskDirector. That is from legal point of view. Where from usability point of view, we also came to a point we have to deprecate it. As DeskDirector expand it's features, there are many settings we have to adjust, and the secret maintenance is also an issue for our customer.
Q: What is issue for secret maintenance?
A: Secret of the application should be short lived, thus Microsoft has been limiting secret's life time to maximum of 2 years, and they also introduced asymmetric key to replace secret. As we keep improve the security, we will eventually move to use asymmetric key rather than secret. As such, the maintenance cost for both DeskDirector and our customer is way too much.
Q: Will DeskDirector remove Custom Application anytime soon?
A: We don't have any specific date been setup, the feature has been deprecated on 15th of Jun 2023, 6 months after its deprecation will be the safe call that there is high chance we will remove it from the system at any point.
Q: Do we need to adjust anything for this deprecation?
A: No, everything should be working as intended, even if we remove the custom application, we will based on existing setup to auto enable default SSO. The only impact will be the end user might encounter consent to view their profile.
Q: How do we minimize impact?
A: You can perform admin consent to grant DeskDirector to read user profile for a specific tenant. You can perform that under company profile page or authentication page. Admin consent will not grant DeskDirector to list users of the tenant, it only allow auto approve consent when a specific user of that tenant request it.
Q: What scopes will DeskDirector ask through admin consent?
A: User.Read, openid, email and profile. You can check what to expect at Microsoft document. During authentication, our application will only ask to read user's profile through User.Read, where openid, email and profile are for desktop application to authenticate user. It uses OAuth's openid to read user's profile, such as primary email.
